WireGuard works great for that.
Max-P
- 1 Post
- 569 Comments

 11·4 days ago
11·4 days agoNot sure if Voyager exposes such a setting (probably?), but on Tesseract I’d do something like this:
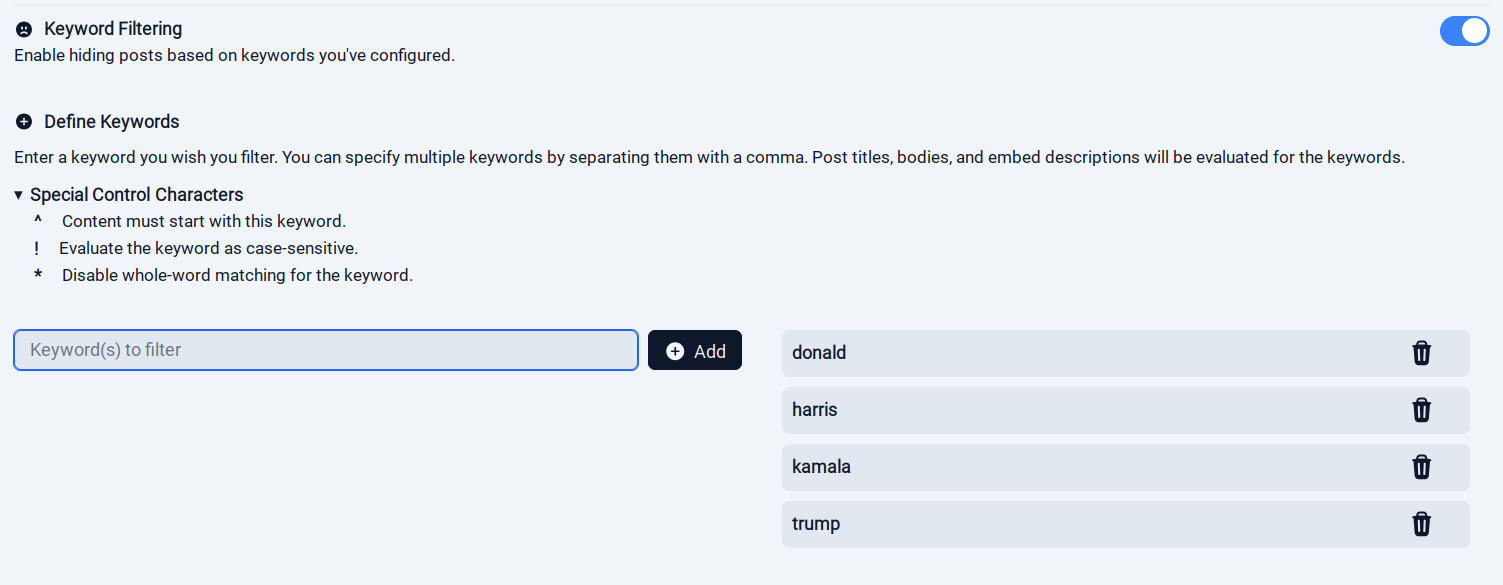

 661·4 days ago
661·4 days agoVoyager for Lemmy, at least for me, pushes political content like crazy.
No content is being pushed to anyone, Lemmy’s algorithms are very simple. It’s just there’s a lot of it.
You can unsubscribe from or block the politics and news communities, especially worldnews, and it should get rid of a lot of it. I find the experience to be better when subscribing to the stuff you want rather than remove the stuff you don’t want.
And also do it now because it’s likely about to get a whole lot more difficult to access to services soon.
I wouldn’t exclude lower IQ as that major of a problem. Sure maybe it kind of excludes you from being an engineer or a lawyer or a doctor and these kinds of jobs. But there’s plenty of low education jobs around, and there’s no shame in that. If everyone was engineers and lawyers we’d have major problems keeping shops and fastfood open. My dad didn’t finish school and raised me no problem, and lives fine. He might not be good at math or writing, but it’s plenty for woodworking and being a handyman.
As others have already pointed out, you’re articulate and sound smarter than a bunch of people I’ve seen on Lemmy. I mean hell, you found your way into Lemmy, a platform that’s still fairly niche and filled with nerds. You could have gone to Reddit but you came to the fediverse.
Everyone have their strengths and things they’re good at. Finding what you like to do is a good start. Some people inherently take artistic paths, and art has nothing to do with intelligence. What you need to do is figure out what you like to do that’s pleasant and satisfying for you to do, and get out of your head that you have to go to higher education.
Also worth noting, you mentioned ADHD. If you’re not diagnosed for it or treated for it, in itself that can significantly lower your IQ scores especially if not accounting for that. When I had my ADHD assessment, they spent time measuring exactly how much my cognitive performance declines under conditions harsh for ADHD. I swear I struggled to figure out how to take the bus after that because I was so fried, was very glad I was too lazy to take the car that day. They noted, initially being well rested I performed really well then my performance tanked the moment they started hammering the ADHD. It’s also important to understand IQ measures only one thing: intelligence. It doesn’t measure empathy, communication, art, or anything else. That might limit you for intellectual jobs, but you can still be great a people jobs. You could be HR, you could be sales, you could be support. Some of the best artists I know failed school hard.
Stop being jealous and ashamed. Those that shame you can go to hell, all they do is make you think you’re worthless and inferior to them. Find your own path.

 2·5 days ago
2·5 days agoYeah it’ll depend on how good your coreboot implementation is. AFAIK it’s pretty good on Chromebooks because Google whereas a corebooted ThinkPad might have some downsides to it.
The slowdowns I would attribute to likely bad power management, because ultimately the code runs on the CPU with no involvement with the BIOS unless you call into it, which should be very little.
Looking up the article seems to confirm:
The main reason it seems for the Dasharo firmware offering lower performance at times was the Core i5 12400 being tested never exceeded a maximum peak frequency of 4.0GHz while the proprietary BIOS successfully hit the 4.4GHz maximum turbo frequency of the i5-12400. Meanwhile the Dasharo firmware never led to the i5-12400 clocking down to 600MHz on all cores as a minimum frequency during idle but there was a ~974MHz.
I’d expect System76 laptops to have a smaller performance gap if any since it’s a first-party implementation and it’s in their interest for that stuff to work properly. But I don’t have coreboot computers so I can’t validate, that’s all assumptions.
That said for a 5% performance loss, I’d say it counts as viable. My games VM has a similar hit vs native. I’ve been gaming on Linux well before Proton and Steam and have taken much larger performance hits before just to avoid closing all my work to reboot for break time games.
You just put both in the
server_nameline and you’re good to go.

 14·7 days ago
14·7 days agoYes dual GPU. I set that up like 6 years ago, so its use changed over time. It used to be Windows but now it’s another Linux VM.
The reason I still use it is it serves as a second seat and is very convenient at that. The GPU’s output is connected to the TV, so the TV gets its own dedicated and independent OS. So my wife can use it when I’m not. When the VM isn’t running I use the card as a render offload, so games get the full power of the better card as well.
I also use it for toying with macOS and Windows because both of those are basically unusable without some form of 3D acceleration. For Windows I use Looking Glass which makes it feel pretty native performance. I don’t play games in it anymore but I still need to run Visual Studio to build the Windows exes for some projects.
This week I also used the second card to test out stuff on Bazzite because one if my friends finally made the switch and I need to be able to test things out in it as I have no fucking clue how uBlue works.

 391·7 days ago
391·7 days agoThe BIOS does a lot less than you’d expect, it doesn’t really have an impact on gaming performance. For what it’s worth, I’ve been gaming in a VM for years, and it uses the TianoCore/OVMF/EDK2 firmware, and no issues. Once Linux is booted, it doesn’t really matter all that much. You’re not even allowed to use firmware services after the OS is booted, it’s only meant for bootloaders or simple applications. As long as all the hardware is initialized and configured properly it shouldn’t matter.

 222·15 days ago
222·15 days agoIt’s nicknamed the autohell tools for a reason.
It’s neat but most of its functionality is completely useless to most people. The autotools are so old I think they even predate Linux itself, so it’s designed for portability between UNIXes of the time, so it checks the compiler’s capabilities and supported features and tries to find paths. That also wildly predate package managers, so they were the official way to install things so there was also a need to make sure to check for dependencies, find dependencies, and all that stuff. Nowadays you might as well just want to write a PKGBUILD if you want to install it, or a Dockerfile. Just no need to check for 99% of the stuff the autotools check. Everything it checks for has probably been standard compiler features for at least the last decade, and the package manager can ensure you have the build dependencies present.
Ultimately you eventually end up generating a Makefile via M4 macros through that whole process, so the Makefiles that get generated look as good as any other generated Makefiles from the likes of CMake and Meson. So you might as well just go for your hand written Makefile, and use a better tool when it’s time to generate a Makefile.
(If only c++ build systems caught up to Golang lol)
At least it’s not node_modules
Yeah, and you’re pinging from server to client with no client connected. Ping from the client first to open the connection, or set keep alives on the client.
Your peer have no endpoint configured so the client needs to connect to the server first for it to know where the client is. Try from the client, and it’ll work for a bit both ways.
You’ll want the persistent keepalive option on the client side to keep the tunnel alive.
They should be in
/run/systemdalong the rest of generated units.
It’s just not that good of a metric overall. Not just because it would be easy to fake it, but also because it would inevitably divide into tribes that unconditionally upvote eachother. See: politics in western countries.
You can pile up a ton of reputation and still be an asshole and still get a ton of support from like-minded people.
The best measure of someone’s reputation is a quick glance and their post history.

 17·19 days ago
17·19 days agoI think it is a circular problem.
Another example that comes to mind: the sanctions on Huawei and whether Google would be considered to be supplying software because Android is open-source. At the very least any contributions from Huawei is unlikely to be accepted into AOSP. The EU is also becoming problematic with their whole software origin and quality certifications they’re trying to impose.
This leads to exactly what you said: national forks. In Huawei’s case that’s HarmonyOS.
I think we need to get back to being anonymous online, as if you’re anonymous nobody knows where you’re from and your contributions should be based solely on its merit. The legal framework just isn’t set up for an environment like the Internet that severely blurs the lines between borders and no clear “this company is supplying this company in the enemy country”.
Governments can’t control it, and they really hate it.

 29·19 days ago
29·19 days agoThe problem isn’t even where the software is officially based, it can become a problem for individual contributors too.
PGP for example used to be problematic because US exports control on encryption used to forbid exporting systems capable of strong encryption because the US wanted to be able to break it when it’s used by others. Sending the tarball of the PGP software by an american to the soviets at the time would have been considered treason against the US, let alone letting them contribute to it. Heck, sharing 3D printable gun models with a foreign country can probably be considered supplying weapons like they’re real guns. So even if Linux was based in a more neutral country not subject to US sanctions, the sanctions would make it illegal to use or contribute to it anyway.
As much as we’d love to believe in the FOSS utopia that transcends nationality, the reality is we all live in real countries with laws that restrict what we can do. Ultimately the Linux maintainers had to do what’s best for the majority of the community, which mostly lives in NATO countries honoring the sanctions against Russia and China.

 42·22 days ago
42·22 days agoThose kinds of problems aren’t particularly new (PGP comes to mind as an example back when you couldn’t export it out of the US), but it’s a reminder that a lot of open-source comes from the US and Europe and is subject to western nation’s will. The US is also apparently thinks China is “stealing” RISC-V.
To me that goes against the spirit of open-source, where where you come from and who you are shouldn’t matter, because the code is by the people for the people and no money is exchanged. It’s already out there in the open, it’s not like it will stop the enemy from using the code. What’s also silly about this is if the those people were contributing anonymously under a fake or generic name, nothing would have happened.
The Internet got ruined when Facebook normalized/enforced using your real identity online.

 11·22 days ago
11·22 days agoThere’s some value in having open-source clients to proprietary services. Of course ideally one would avoid using them, but since many are stuck with games they already purchased and the launcher was bolted on later in an update, it makes sense.
At the very least it probably doesn’t implement a lot of the telemetry, and it doesn’t require you to figure out how to make the launcher work under Proton, only the game.
Less proprietary is better than nothing.

 321·24 days ago
321·24 days agoEveryone’s approaching this from the privacy aspect, but the real reason isn’t that the cashier thought you were weird, they’re just underpaid and under a lot of pressure from management to try multiple times and in some cases they even get written up for not doing it because it’s deemed part of their job. They hate it just as much as you. Same when you try to cancel your cable subscription or whatever: the calls are recorded and their performance is monitored and they make damn sure they try at least 3 times to upsell you, even when it’s painfully obvious you’re done with them.
Just politely decline until they asked however many times they’re required to ask and move on.

It’s the same as glxgears but for EGL and Wayland. It tests that OpenGL works.